The Department of Energy’s Cybersecurity, Energy Security, and Emergency Response Office (CESER) has partnered with Idaho National Laboratory (INL) to lead a research initiative, called CyOTE, that addresses energy sector cybersecurity threats against operational technology (OT) environments. Through coordinated research with the national lab complex and energy sector companies, researchers analyze ICS/OT attack surfaces, develop new capabilities to evolve the national OT Cybersecurity posture, and share information about adversarial tactics and techniques. CyOTE improves the sector’s ability to detect and respond to anomalous behavior that indicates potential malicious activity in OT networks.
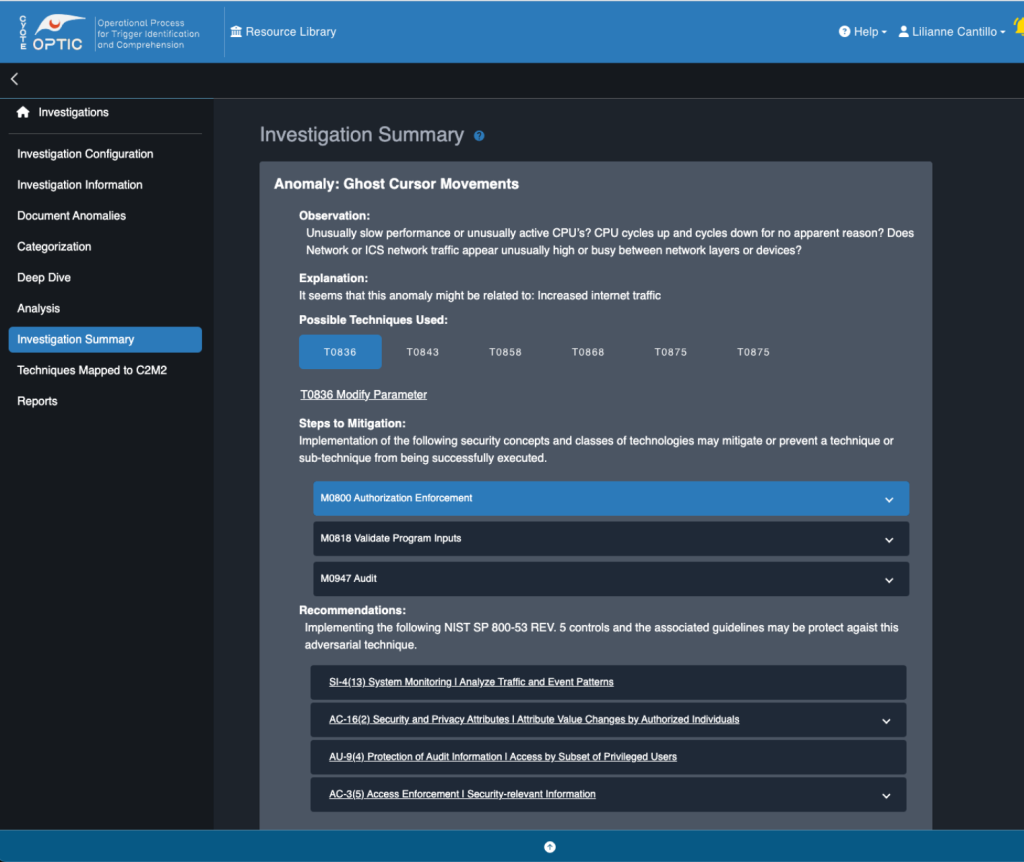
OT applications, radio frequency (RF) environments, OT supporting infrastructure and connecting wired and wireless networks are increasingly becoming targets of cyberattacks. These attacks can have devastating consequences, such as disruption to energy supplies, damage to critical infrastructure, significant financial loss, and risk to human life. CyOTE can be used as a methodology and a suite of supporting tools to aid in the protection of OT networks in the energy sector.
CyOTE provides a number of benefits to the energy sector, including:
Disclaimer: By requesting / accessing these free tools, you agree that you will not use or modify the tool(s) for commercial purposes.
The cybersecurity tools used for information technology (IT) environments cannot equally protect the operational technology (OT) environment from cyber threats.